ledger.com/start — A Step-by-Step Guide to Securing Your Crypto
Cryptocurrency offers exciting opportunities, but it also comes with risks. Hacks, phishing, and accidental loss of keys can turn your digital wealth into permanent loss. Ledger hardware wallets provide a safe way to protect your crypto, and the official starting point, ledger.com/start, ensures you set up your wallet securely and correctly.
In this guide, we’ll take you from the moment you unbox your Ledger device to mastering advanced security practices, giving both beginners and mid-level users the confidence to safeguard their digital assets.
Why Ledger is the Gold Standard in Hardware Wallets
Imagine keeping your cash in a vault that only you can access. Ledger wallets serve a similar purpose for your crypto. They store private keys offline, making them immune to online hacks or malware.
Benefits of Ledger wallets include:
- Offline key storage: Private keys never touch the internet.
- Multi-coin support: Compatible with hundreds of cryptocurrencies.
- Verified security: Firmware and apps are open-source and regularly audited.
- Ease of management: Ledger Live app simplifies everything from setup to daily transactions.
Ledger offers two main devices:
- Ledger Nano S: Perfect for beginners; compact and affordable.
- Ledger Nano X: Advanced model with Bluetooth, larger storage, and mobile compatibility.
Step 1: Begin Safely at ledger.com/start
The journey begins at ledger.com/start, the official portal to set up your Ledger device. Using this site ensures you download official software and follow secure instructions, avoiding phishing sites that try to steal your recovery phrase.
At the portal, you can:
- Identify your Ledger device model.
- Download Ledger Live for desktop or mobile.
- Access step-by-step instructions for initialization and setup.
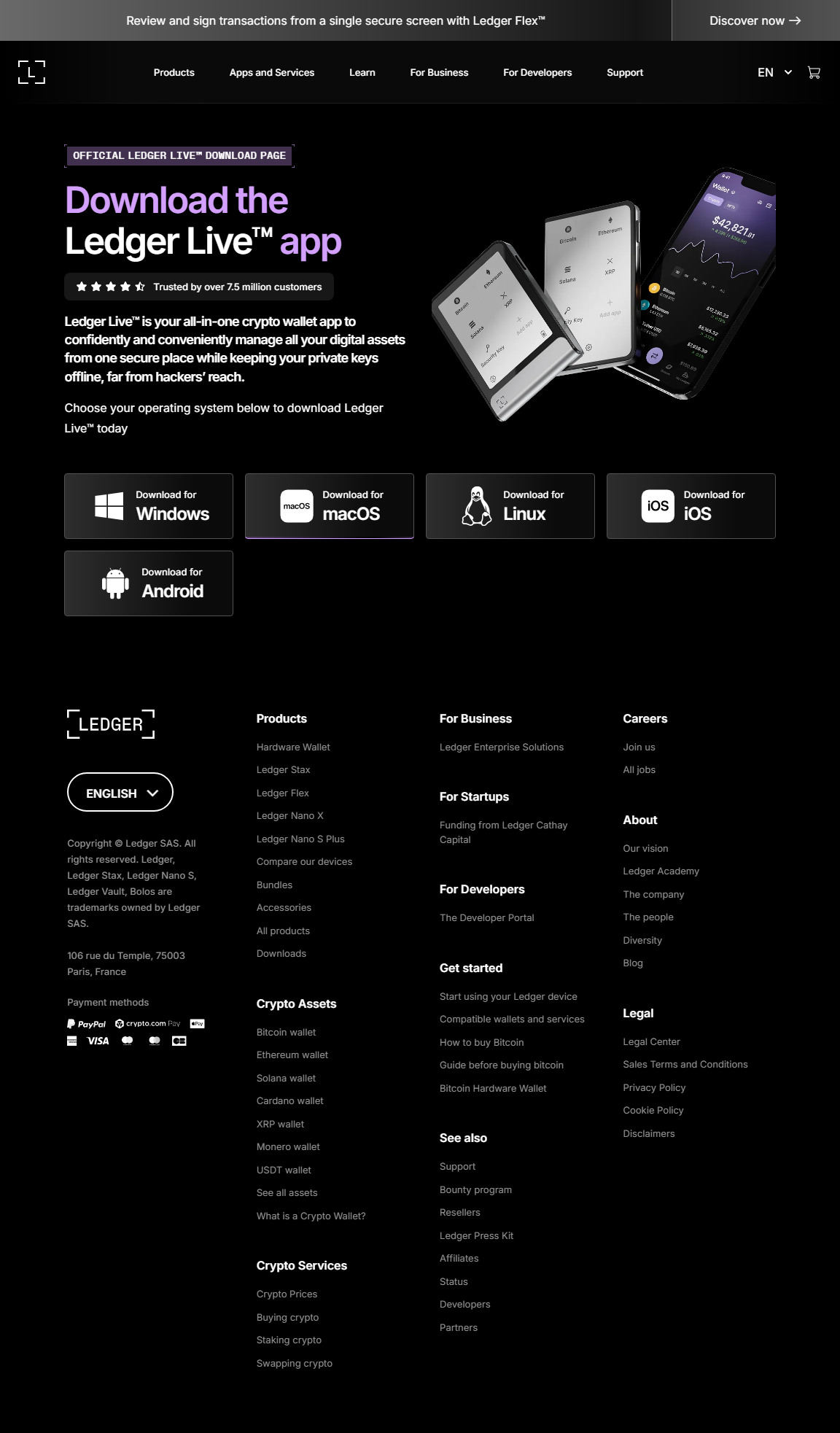
Step 2: Installing Ledger Live
Ledger Live is the app that allows you to manage your cryptocurrency securely. It works on Windows, macOS, Linux, and mobile devices. From Ledger Live, you can view balances, send and receive crypto, install apps for coins, and update firmware.
Installing Ledger Live
- Visit ledger.com/start and download the Ledger Live app for your device.
- Install the software following the on-screen instructions.
- Connect your Ledger device and open Ledger Live.
Ledger Live will automatically detect your device and guide you through secure setup instructions.
Step 3: Initializing Your Ledger Device
Initialization is a critical security step. It includes installing firmware, creating a recovery phrase, and setting a PIN.
Firmware Installation
Ledger devices ship without firmware for security reasons. Ledger Live downloads verified firmware directly from Ledger servers. Always check the source to prevent malicious installations.
Generating Your Recovery Phrase
During setup, your Ledger will display a 24-word recovery phrase. Write it down on the provided sheet and store it offline in a secure location. This is your only backup — losing it means losing access to your crypto.
Setting a PIN
Your PIN protects your wallet from unauthorized access. Enter a combination that is secure yet memorable. The device will request this PIN every time it connects.
Step 4: Managing Your Wallet via Ledger Live
Once your device is initialized, Ledger Live becomes your dashboard. From here, you can:
- Check balances for all supported coins.
- Send and receive cryptocurrency securely.
- Install coin-specific apps.
- Monitor transactions and portfolio performance.
Every transaction must be confirmed on the device, so malware on your computer cannot move funds without your authorization.
Advanced Security Tips
1. Use Passphrase-Protected Accounts
Ledger allows you to create hidden wallets with passphrases. Even if someone knows your recovery phrase, they cannot access a hidden wallet without the passphrase.
2. Multiple Devices and Wallets
You can manage multiple Ledger devices or multiple wallets with separate recovery phrases for organization and enhanced security.
3. Regular Firmware Updates
Firmware updates fix vulnerabilities and add support for new coins. Always update using Ledger Live to ensure authenticity.
4. Integration with Third-Party Wallets
Ledger is compatible with wallets like MetaMask, MyEtherWallet, and Electrum, allowing advanced users to manage additional tokens while keeping private keys offline.
Common Mistakes to Avoid
- Never store your recovery phrase digitally or online.
- Only download Ledger Live from ledger.com/start.
- Verify firmware authenticity before installing.
- Disconnect the device when not in use.
- Enable passphrase protection for high-value funds.
Maintaining Your Ledger Wallet
- Keep your recovery phrase in a secure, offline location.
- Update firmware regularly.
- Use passphrases to create hidden wallets for sensitive assets.
- Disconnect the device when not actively using it.
FAQ: ledger.com/start
1. Is ledger.com/start safe?
Yes, it’s the official Ledger setup portal. Always ensure the URL is correct and secured with HTTPS.
2. Can I use Ledger without Ledger Live?
Technically yes, but Ledger Live simplifies setup, management, and security for beginners.
3. What happens if I lose my Ledger?
You can restore your wallet using the 24-word recovery phrase. Without it, your crypto is lost permanently.
4. Does Ledger support all cryptocurrencies?
Ledger supports hundreds of coins, though some tokens may require third-party wallets.
5. How often should I update Ledger firmware?
Check Ledger Live frequently for updates. Firmware updates ensure your device stays secure and compatible with new coins.
6. Can I use a passphrase for extra security?
Yes. Passphrases create hidden wallets that provide an extra layer of protection.
Conclusion
Starting your cryptocurrency journey with Ledger via ledger.com/start ensures maximum security from day one. The portal guides you through setup, firmware updates, and security best practices, helping both beginners and mid-level users confidently manage their crypto assets. By following the official process, you maintain full control over your funds while keeping them safe from online threats.